This blog is about an Interesting CTF challenge that I solved a few months back. This challenge is from the famous PEACTF 2019 and It was the last challenge of the CTF.
The Name of the challenge is “Phillips And Over (Web 900 points)”.
Description: There is a website running at http://shell1.2019.peactf.com:55534. Try to log in to the "admin" account.
This is a web exploitation challenge with a login page. From the above description, we got the username for the login page as “admin”. If you think of brute-forcing then it will take weeks to complete this challenge. There was a reset password option which seemed to be an easy way.

Here we can give the username and the answer to the security question which we obviously don’t know. I tried some guesses for the security question, but everything led me to an empty page. Then I started inspecting the page where I found an interesting field hidden on the HTML code. A field named “debug” with value “0” was hidden.

I changed the value to “1” and tried guessing again, but nothing works. Ok, then I was done with all the educated guessing part. Testing for SQL injection Vulnerability with “debug” value “0” gave the same blank page. Testing with the “debug” value “1” gave the necessary SQL errors.
That’s it, SQL Vulnerability!!!!

Manual SQL exploitation is always an Interesting thing but quite time-consuming.
I sat on Manual exploiting over this for hours but, then I wanted to complete this one as soon as possible so I went with the tool called “sqlmap”
Now we know the vulnerable parameters all we need to do is to feed it to the “sqlmap”

Now we have identified the SQL database being used, it’s time to enumerate the columns
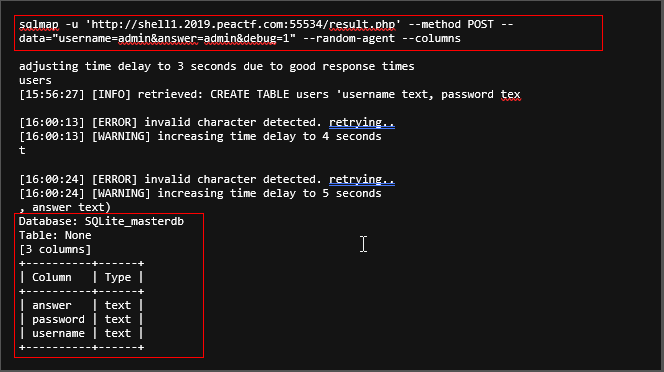
Now we got the required columns from the database, let’s dump them

Now we have both Password and Answer to the “admin”
Now we use any of these to get our flag

Flag : flag{peactf_E_>_A_778d32cbfc538c54867ef5956cbf4bf1}
This was a good 900 point and learned something new about tampering fields on HTML page.