An Adobe zero-day vulnerability is being exploited in the wild in targeted attacks against Windows users in the Middle East. The Flash Player flaw is indexed as CVE-2018-5002. It is a stack-based buffer overflow bug that enables attackers to execute arbitrary code. This vulnerability resides in the interpreter code of the Flash Player that handles static-init methods, which incorrectly the exceptions for try/catch statements. The attack leverages Microsoft Office documents with embedded malicious Flash Player content scattered through Spear Phishing. This flaw is very critical in nature and it is advised to follow the recommendations mentioned in this document. This advisory describes an outline of various aspects of the attack, the potential targeting of Qatar, and suggestions for defenses. For more information please refer to VSintelli1.
Attack Sketch
The exploit makes use of a Microsoft Office document to download and execute an Adobe Flash Player exploit to the victim systems.

Fig 1. Exploitation Process
The exploitation process begins by downloading and executing a remote Shockwave Flash file (SWF). Most of the exploits are delivered with Microsoft Office, this attack sketch includes the SWF content directly embedded in the document.
The first stage SWF includes RSA+AES cryptosystem that protects the subsequent stage which contains the actual exploit, that downloads and executes.
The second SWF stage after exploiting the system and achieving code execution uses the same cryptosystem to download and execute the shellcode to enable the threat actor to control the victim machine.
Remote Flash Inclusion
The attack loads the Adobe Flash player from within the Microsoft Office. Attackers embed a Flash file within a document, which contains the entire exploit, or may stage the attack to download the exploits. This leaves a small Flash loader that defenders can flag for detection and analysts can use for tracking.
The following figure (Fig2) shows how the SWF file can be embedded inside the Microsoft Document.

Fig 2. Example Flash object included via “Movie” property which specifies the remote location of Flash object
Cryptographic Routines
Data transmission from the attacker’s server to the client is protected by a custom cryptosystem leveraging a symmetric cipher (AES), that protects the payload and an asymmetric cipher (RSA) to protect the symmetric key.

Fig 3. Generic network retrieval and decrypt routine
Data Transmission is initiated by the client, whereby the client HTTP POSTs a randomly generated RSA modules n and the exponent 0x10001, and the server responds with the following structure.
0x0: Encrypted AES key length (L)
0x4: Encrypted AES key
0x4+L: AES IV
0x14+L: AES encrypted data payload
To decrypt the data payload, the decryption process of the client has two steps
- Decrypting the encrypted AES key using its randomly generated private key
- Decrypts the data payload with the decrypted AES key.
Use of Zero-Day Exploit
After decryption, the exploit payload is loaded and triggered to allow for follow-on code execution. Although the document is a Microsoft Office document, the code is executing within an Adobe Flash container.
Network Communications
During the attack, the weaponized document downloads the initial SWF and multiple parts of the encrypted data from the attacker’s server and provides basic system information to the same server, both over HTTP.
All the downloads include a 32-byte unique parameter named ‘token’, that is reused in the URI paths of other URLs passed as Flash parameters.
The SWF stages log data to the URL identified as 'stabUrl', which is on the same command-and-control server. The URI is constructed by appending a random value onto a format string
stabUrl + “%d - %d- %d . png?x=” + Math.random()
whose values will indicate the current function, and progress within the function.
Once that is completed, a request is made to the 'encKeyUrl' parameter, which is the second stage SWF containing the exploit. Upon retrieval of the second stage, a request is then made to the 'downloadUrl', which is the shellcode payload.
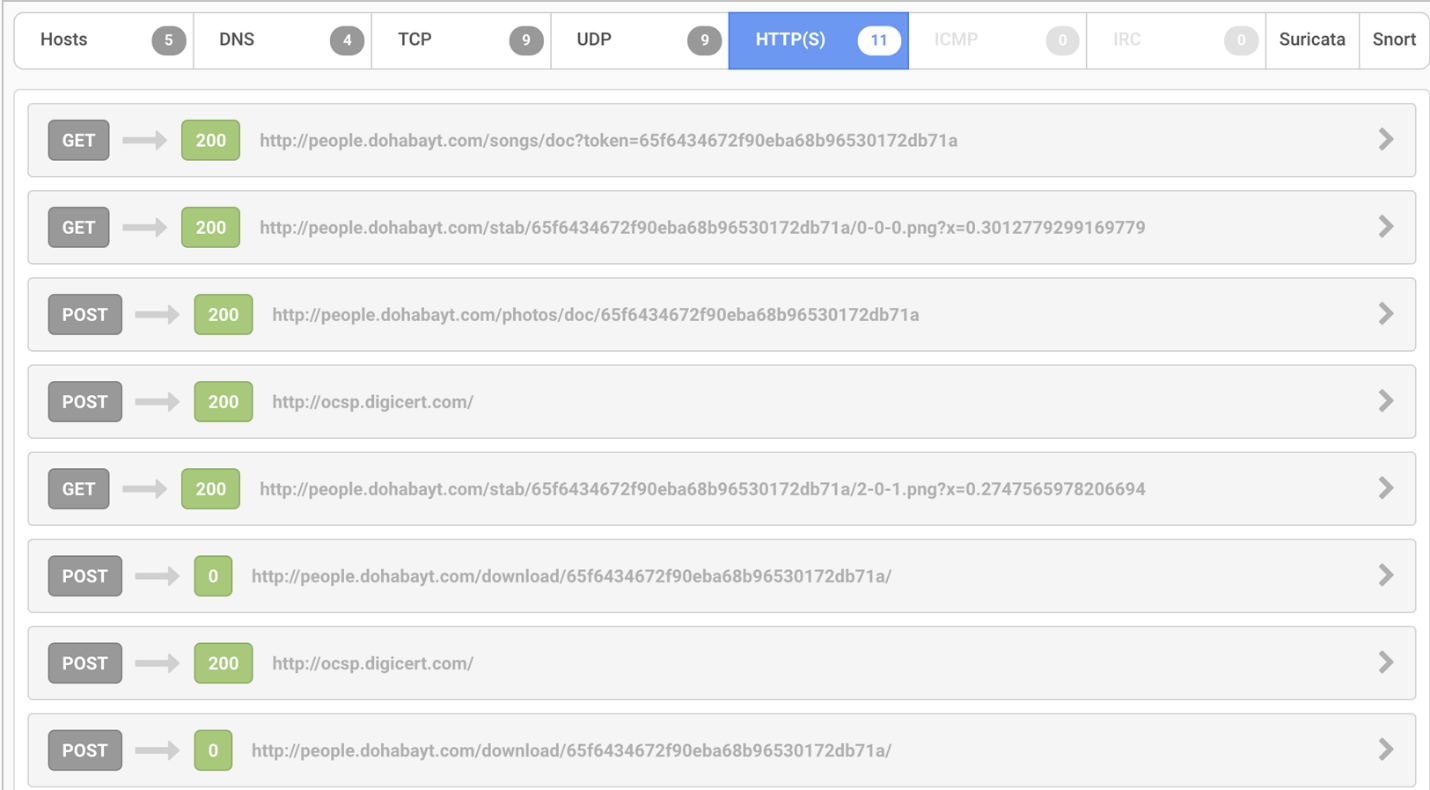
Fig 4. Network Communications observed during the analysis

Fig 5. Network trace of HTTP requests
Possible Qatari Targeting
The weaponized document titled “الراتب الاساسي.xlsx” (translated to “basic_salary”), is an Arabic language themed document that purports to inform the target of employee salary adjustments. The document was uploaded from an IP address in Qatar to VirusTotal on May 31, 2018. Most of the job titles included in the document are diplomatic in nature, specifically referring to salaries with positions referencing secretaries, ambassadors, diplomats, etc.

Fig 6. Weaponized document in Arabic purporting to show salary modifications
Within the document, the threat actor utilizes the domain ‘dohabayt[.]com’ for malicious content which also reveals additional clues as to the intended target. When broken down into parts, the domain indicates a possible targeting of Qatar interests.
The first part contains “doha”, which is the capital of Qatar. The second part also may be mimicking the legitimate Middle Eastern job search site “bayt[.]com” in a further attempt to blend in on the network.

Fig 7. Attacker domain broken down into pieces
Affected Versions
The following versions are vulnerable-
- Adobe Flash Player 29.0.0.171 and prior versions for Desktop Runtime, Google Chrome, Microsoft Edge and Internet Explorer 11.
Indicators of Compromise
Hashes
0b4f0d8d57fd1cb9b4408013aa7fe5986339ce66ad09c941e76626b5d872e0b5
6535abc68a777b82b8dca49ffbf2d80af7491e76020028a3e18186e1cad02abe
Malicious Domains
people.dohabayt[.]com
internationsplanet[.]com
Malicious IP Addresses
185.145.128.57
Immediate Actions to Follow
- System Administrators are advised to apply the appropriate updates.
- System Administrators are advised to monitor the critical systems and allow only trusted users to have the network access.
- System Administrators are advised to disable the Flash Player Plugins.
- Users are advised not to open email messages from suspicious or unrecognized sources. If users are not able to verify the links or attachments, they are advised not to open them.
- Users are advised to use an unprivileged account when browsing the Internet.
References
[1] VSintelli Adobe Flash Player CVE-2018-5002 Stack Based Buffer Overflow Vulnerability PCS-2018-02522
http://vsintelli.com/portal/cve_preview.php?cid=2528
[2] Security updates available for Flash Player | APSB18-19
https://helpx.adobe.com/security/products/flash-player/apsb18-19.html
[3] Flash Player Desktop Runtime version 30.0.0.113 for Windows, macOS and Linux
https://get.adobe.com/flashplayer/
[4] Flash Player for Google Chrome version 30.0.0.113 for Windows, macOS, Linux and ChromeOS
https://chromereleases.googleblog.com/
[5] ADV180014 | June 2018 Adobe Flash Security Update
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV180014
[6] Adobe Flash Player Stack-Based Buffer Overflow Arbitrary Code Execution Vulnerability
https://tools.cisco.com/security/center/viewAlert.x?alertId=58087&vs_f=Alert%20RSS&vs_cat=Security%20Intelligence&vs_type=RSS&vs_p=Adobe%20Flash%20Player%20Stack-Based%20Buffer%20Overflow%20Arbitrary%20Code%20Execution%20Vulnerability&vs_k=1
[7] Adobe Releases Security Updates for Flash Player
https://www.us-cert.gov/ncas/current-activity/2018/06/07/Adobe-Releases-Security-Updates-Flash-Player
[8] Multiple Vulnerabilities in Adobe Flash Player
https://cert.be/fr/docs/multiples-vuln%C3%A9rabilit%C3%A9s-dans-adobe-flash-player.html
[9] Adobe Flash Zero-Day Leveraged for Targeted Attack In Middle East
https://www.icebrg.io/blog/adobe-flash-zero-day-targeted-attack